CIA
(confidentiality, integrity & availability) is the most important concept
of Cybersecurity, although many people may interpret it wrong.
It is not
entirely clear when it was the first time CIA-triad was used. It was apparently put
to use in 1998, when Don Parker wrote about it in his book "Fighting
Computer Crime". Confidentiality is probably the oldest one. The term comes
from US army when they decide to tag computer information in the same
classification as old paper documents.
The underlying
idea of the CIA is that we always look at Confidentiality, Integrity, and Availability when defining the
information security of data and systems.
The
high-level definitions
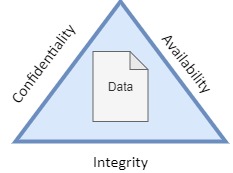
Confidentiality: Define the need to protect the data
from being exposed to an unauthorized person.
Integrity: Define how we verify that the data
was not modified and is reliable
Availability: Define how we ensure that the data
will be accessible when required and not removed without permission.
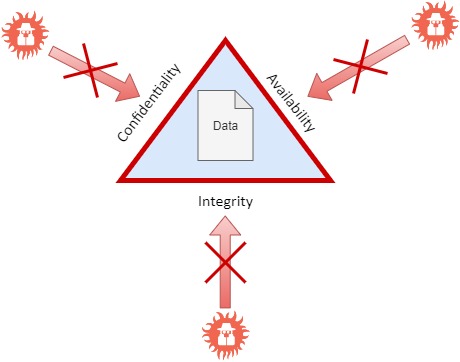
The CIA
triad comes to help you remember that all three sides of the triangle encompass the data between them.
When doing your
threat modeling, you should look at it in the following way:
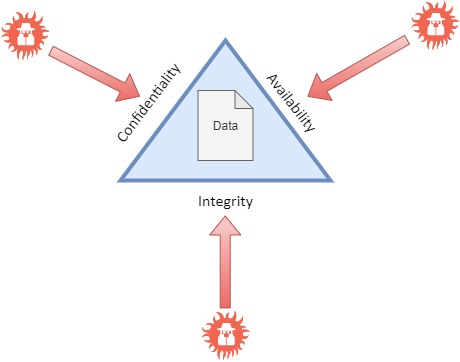
That means
you need to think about how you protect your data against attacks on each of
the CIA-triad sides
This action
will help you cover the proper security controls to protect your data.
Remember,
there are three key points you need to take into account while planning how to
protect your data. Using only one of them will not be satisfactory.
For example:
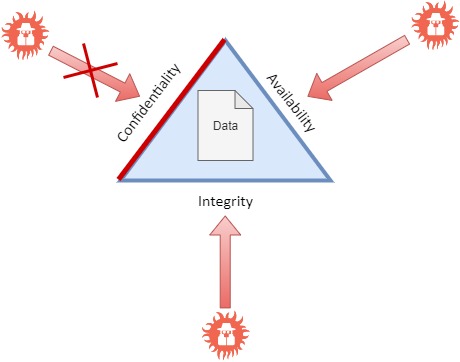
"Dream
Bank" defines that the customer account’s data needs to be protected;
therefore, the security action to protect it is encryption.
This covers only Confidentiality.
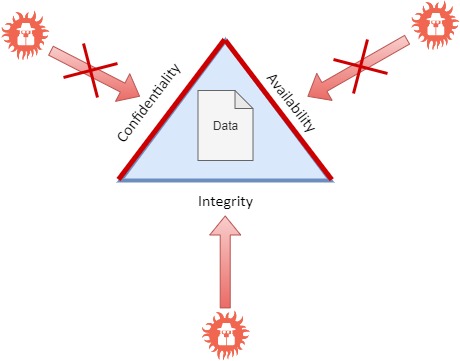
When Dream
Bank Security Persona looks at the Availability, it thinks about the
following case:
"What
will happen if our DB that holds customer account’s data is damaged? Will we be
able to keep the data available to the customer?"
The Security
Persona defines the following security requirement:
"The DB
needs to be part of a Cluster, with Active-Passive functionality, so in case
one DB failed, the cluster will still work"
This will
cover the Availability requirement.
When Dream
Bank Security Persona looks at Integrity, it thinks about the following
case:
"Can we
guarantee the customer that the amount of money he has in his account can't be
manipulated?"
Security
Persona defines the following security requirement:
"The
customer amount of money can be updated only by deposit or withdrawal
methods, and these methods must be logged and documented"
This will cover the Integrity
requirement.
Important
note: This is
simplified set of requirements. In real life you will usually need to define
more than one requirement.
Stay safe,
Tomer