Security personnel dealing with "Threat Modeling" are familiar with "DFD" and "threat model". To align with all readers, I will first explain these terms briefly.
Threat Modeling:
"Threat modeling is a process by which potential threats, such as structural vulnerabilities or the absence of appropriate safeguards, can be identified and enumerated, and countermeasures prioritized.[1] The purpose of threat modeling is to provide defenders with a systematic analysis of what controls or defenses need to be included, given the nature of the System, the probable attacker's profile, the most likely attack vectors, and the assets most desired by an attacker. Threat modeling answers questions like "Where am I most vulnerable to attack?", "What are the most relevant threats?", and "What do I need to do to safeguard against these threats?"."
(From https://en.wikipedia.org/wiki/Threat_model)
DFD (Data Flow Diagram):
"A data-flow diagram is a way of representing a flow of data through a process or a system (usually an information system). The DFD also provides information about the outputs and inputs of each entity and the process itself. A data-flow diagram has no control flow — there are no decision rules and no loops. Specific operations based on the data can be represented by a flowchart"
(From https://en.wikipedia.org/wiki/Data-flow_diagram)
To simplify it, Threat Modeling is when we look at our System (product/application/etc.) and try to find potential security flaws and/or security risks. To easily understand how our system is composed and how data flows in the system, we use the DFD.
The DFD, is a visual way to present from what the system is composed, which process communicates with which process, what is the "outside" world of our system.
I encourage you to learn more about these terms, you will find plenty of information over the Internet.
Now, when we more or less understand what "Threat Modeling" is and what is "DFD" (Data Flow Diagram), let me explain what are the DFD levels (DFD-0, DFD-1, and DFD-2).
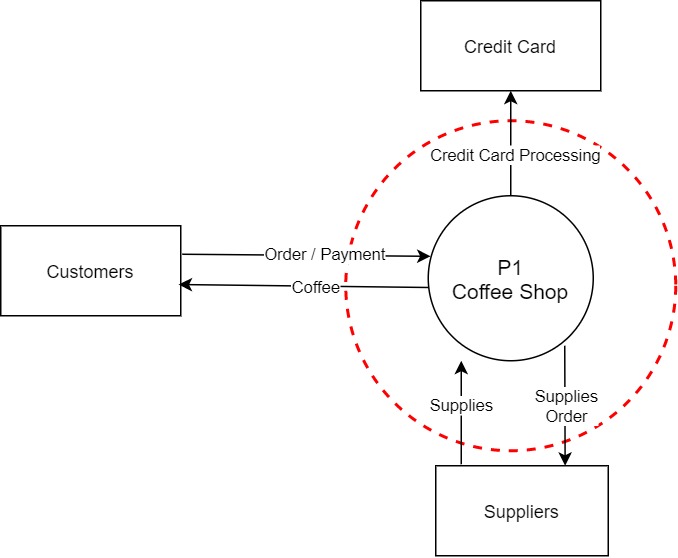
DFD level 0 (DFD-0): Also known as "DFD Context", in this level, we place our system as one process in the center and focus on inbound and outbound from external elements.
Example of a DFD of a coffee shop:
The main process is P1 (Coffee Shop), the red dotted cycle represents our trusted zone ( I will talk about it later)
Threat Modeling:
"Threat modeling is a process by which potential threats, such as structural vulnerabilities or the absence of appropriate safeguards, can be identified and enumerated, and countermeasures prioritized.[1] The purpose of threat modeling is to provide defenders with a systematic analysis of what controls or defenses need to be included, given the nature of the System, the probable attacker's profile, the most likely attack vectors, and the assets most desired by an attacker. Threat modeling answers questions like "Where am I most vulnerable to attack?", "What are the most relevant threats?", and "What do I need to do to safeguard against these threats?"."
(From https://en.wikipedia.org/wiki/Threat_model)
DFD (Data Flow Diagram):
"A data-flow diagram is a way of representing a flow of data through a process or a system (usually an information system). The DFD also provides information about the outputs and inputs of each entity and the process itself. A data-flow diagram has no control flow — there are no decision rules and no loops. Specific operations based on the data can be represented by a flowchart"
(From https://en.wikipedia.org/wiki/Data-flow_diagram)
To simplify it, Threat Modeling is when we look at our System (product/application/etc.) and try to find potential security flaws and/or security risks. To easily understand how our system is composed and how data flows in the system, we use the DFD.
The DFD, is a visual way to present from what the system is composed, which process communicates with which process, what is the "outside" world of our system.
I encourage you to learn more about these terms, you will find plenty of information over the Internet.
DFD level 0 (DFD-0): Also known as "DFD Context", in this level, we place our system as one process in the center and focus on inbound and outbound from external elements.
Example of a DFD of a coffee shop:
The main process is P1 (Coffee Shop), the red dotted cycle represents our trusted zone ( I will talk about it later)
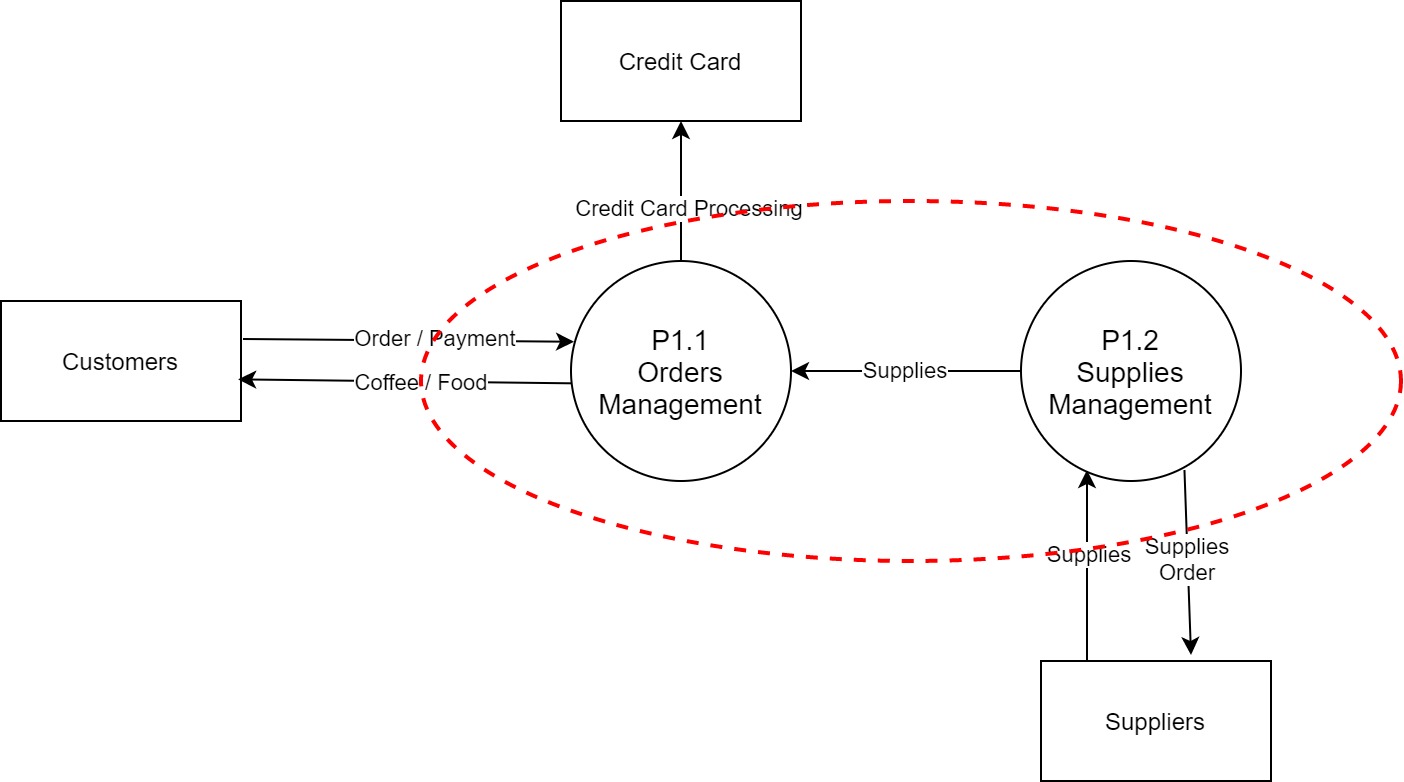
DFD Level 1 (DFD-1): Decomposed of DFD-0 to a main business process. It usually represents the main functional areas of the system.
In our example, we took our Coffee Shop(P1) and separated it into 2 main processes P1.1 (Order Management) and P1.2 (Supplies Management).
As you can see, our trusted zone is still the same (contain all "break-down" of the main process)
In our example, we took our Coffee Shop(P1) and separated it into 2 main processes P1.1 (Order Management) and P1.2 (Supplies Management).
As you can see, our trusted zone is still the same (contain all "break-down" of the main process)
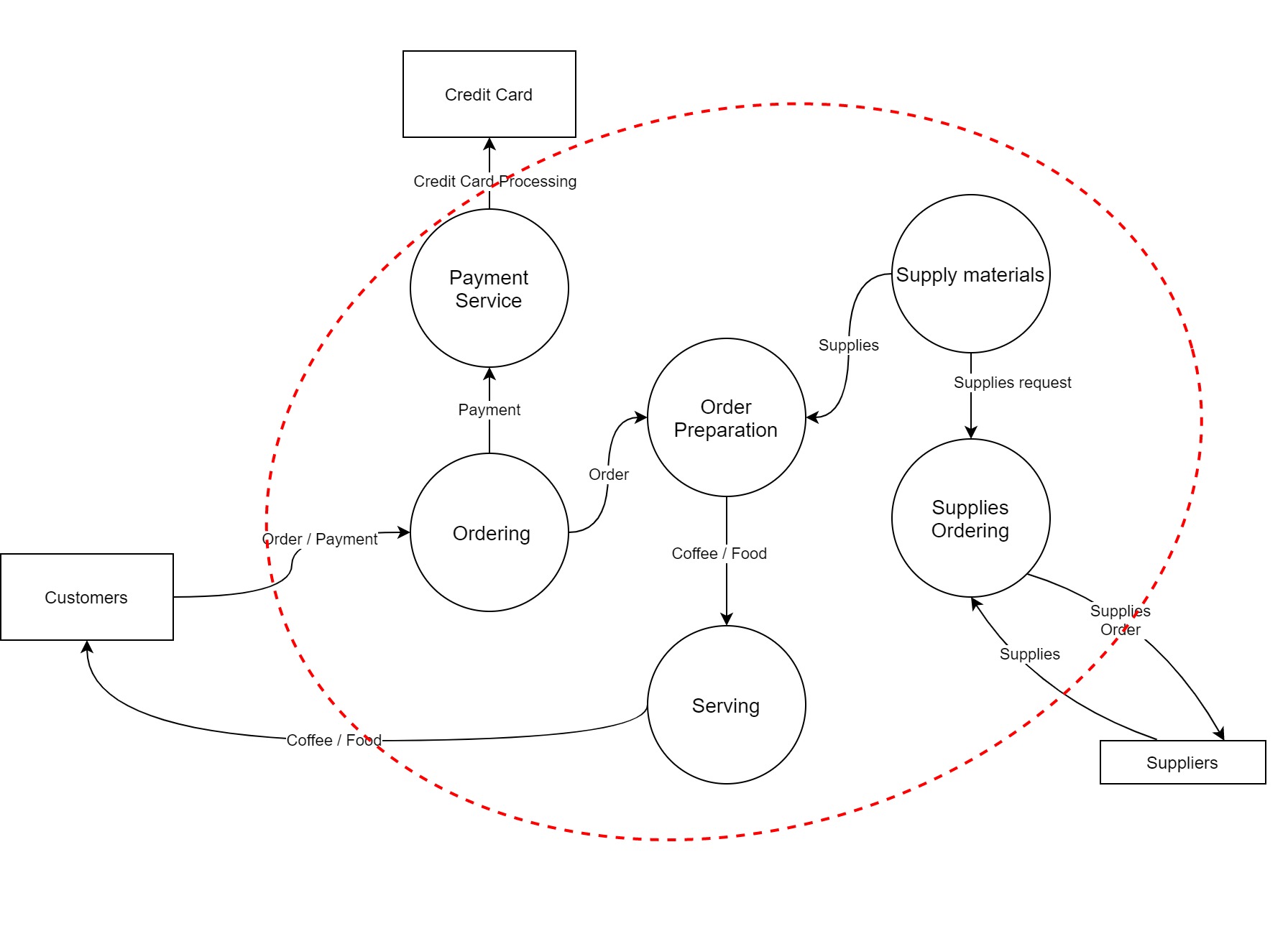
DFD level 2 (DFD-2): Decomposed of DFD-1 (same as DFD-1 is to DFD-0), although, usually in this level, we start looking at the level of services.
In our example, we will break each process into services.
So, how does the DFD level impact the Threat Modeling?
First, the higher the DFD level is, it includes more details, therefore, it better exposes the components, the communications, and the type of data flow between all components.
It also allows us to support the Zero-Trust approach. When we use DFD-0, we look at the system as one that is protected from the "outside world". When you drill down- to the DFD-2, it allows you to see each service as a single protected unit and also exposes threats from internal actors.
To summarize it up, as you drill down in your DFD (0->1->2), you will have better visibility of your system. This will lead to better threat modeling, which in turn, leads to improving your system security posture.
Stay safe,
Tomer