Social engineering plays a crucial part in the Kill-Chain. Attackers
will use social engineering to compromise and get access to the organization
they are targeting.
Kill Chain is combined from 7 phases as you can see from the
below figure:
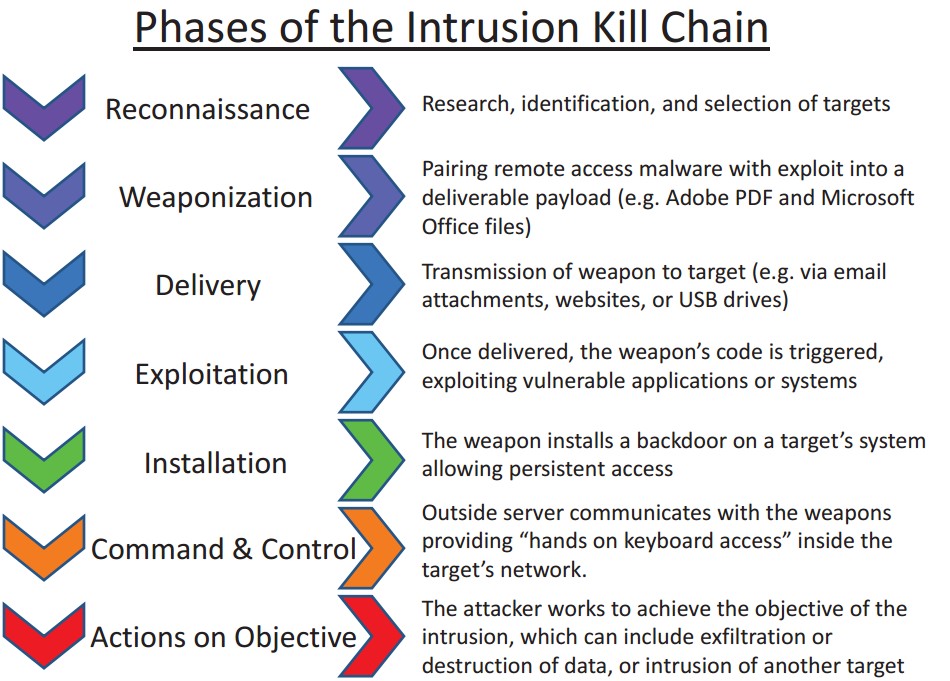
Original Lockheed Martin Cyber (Intrusion) Kill Chain
Social engineering takes part in the first 5 phases.
In the following example, I will present the use case and
each phase and its social engineering impact
As an example, the organization that is targeted for attack
will be “Dream Bank” (not a real bank).
Bob is a bank teller who likes social media.
Phase 1 Reconnaissance:
Step 1 : Search targeted employees with positions that
have access to the bank’s network.
The attacker looks for an employee that works for “Dream
Bank”, an employee that shares posts in “Dream Bank’s” Facebook page.
Attacker also searchs LinkedIn for persons that define themselves
as “Dream Bank” employees.
This step brings a list of potential targets, one of them is
Bob.
Step 2 : Attacker starts to look for information on
Bob, he finds that Bob has many posts on Facebook.
The attacker has found 2 important posts.
1.
“Like any day, I arrived
exactly at 8 AM to my loved work in 'Dream Bank' on 27th street”
2.
“Madonna is the best!!, I
like to hear her while I am working and need to increase my motivation”
Let’s get into the Attacker’s head and analyze the posts
First Post:
· “Like any day, I arrived
exactly at 8 AM” –
Time schedule, now I know that Bob arrives at work every day
at 8 AM.
· “work in “Dream Bank” on 27th
street”- Location, now I know where he
works.
Second Post:
· “Madonna is the best!!” –
Bob admires Madonna
· “I like to hear her while I
am working and need to increase my motivation” –
Bob likes to hear Madonna at
work
Step 3: Look for Infrastructure weaknesses
Attacker uses search engines to find articles that talk
about computers and are used in “Dream Bank”.
Attacker finds a couple of results that present employees
complaints about having to use such old computers, computers that still have
CD-ROM drive.
Phase 2 Weaponization:
Based on the reconnaissance results, attacker decides that
the remote access malware will be hidden inside Madonna’s disk.
Logic: Bob likes Madonna + the organization still has CD-ROM
in their computers
Attacker creates a CD-ROM that includes the latest disk of Madonna
and also the remote access malware.
To make it more trustable he prints a label like on the
original disk and pastes it on the disk.
Phase 3 Delivery
· Based on Phase 1 and 2 – attacker now needs to deliver the
CD-ROM to Bob.
· Attacker knows where Bob works, and when Bob gets to work.
· On Monday at 8 AM he waits for Bob near his workplace.
· He calls him, says “Sorry sir, it seems to me that you have
dropped a disk".
· Bob is in a hurry to get to work, sees that it's the Madonna
disk he loves.
· Although he's not sure it's his, he takes the disk.
· After all he likes to hear Madonna, and he really has a disk
like that,
so it makes sense that it fell out of his bag.
Phase 4 Exploitation
Bob, happy about the disk, logs in to his computer, inserts
the CD-ROM and plays the disk.
Phase 4 Installation
Without Bob even knowing, the malware installed itself on
Bob’s computer.
Currently the attacker has malware installed on a “Dream
Bank’s” computer inside the bank’s network.
In future posts, I will talk about the next phase Command
& Control, and how the attacker continues the attack.
Stay safe,
Tomer