This post will talk about how a social engineering attack succeeds and how attackers think. If you understand how they think, you may detect and prevent the next attempt.
You may ask yourself “Why will I be the target of a social engineering attack?”
If you fall in one the following categories, you are a potential target:
1. You work for an organization that holds data
3. You have a credit card that can be charged online
4. You have an identity that can be stolen and used by someone else
As you can see, anyone falls into one of the above categories.
When you are targeted, by attackers, they start to gather information about you.
After an attacker learns about you, he/she will try to find your “weakness” points. These “weakness” points may be different from one person to another. Couple of examples:
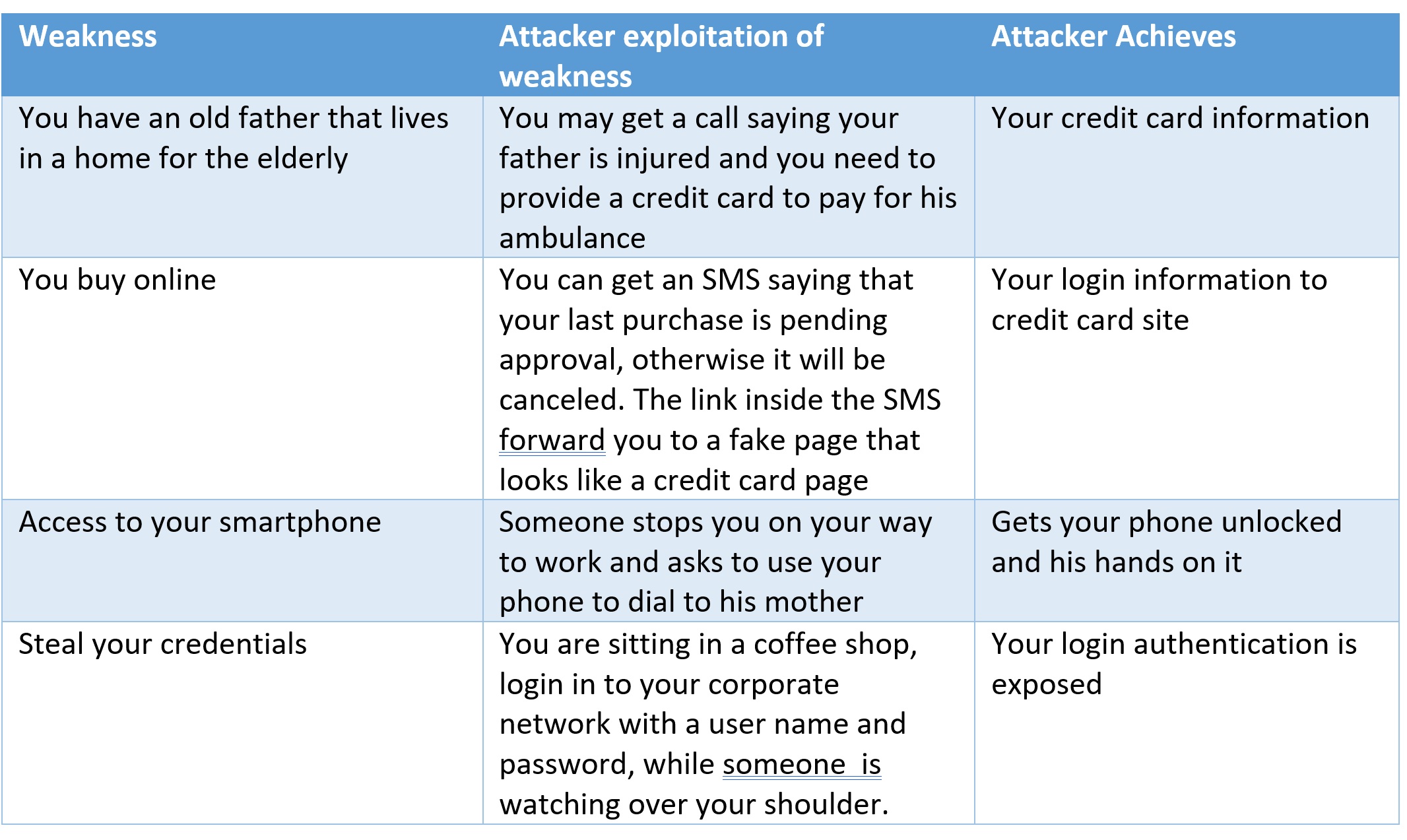
Now, I guess, you can understand how easy it is to fall into a social engineering scam.
As easy as it looks, it is easy to avoid it. Let’s look at same examples and how to secure our actions.
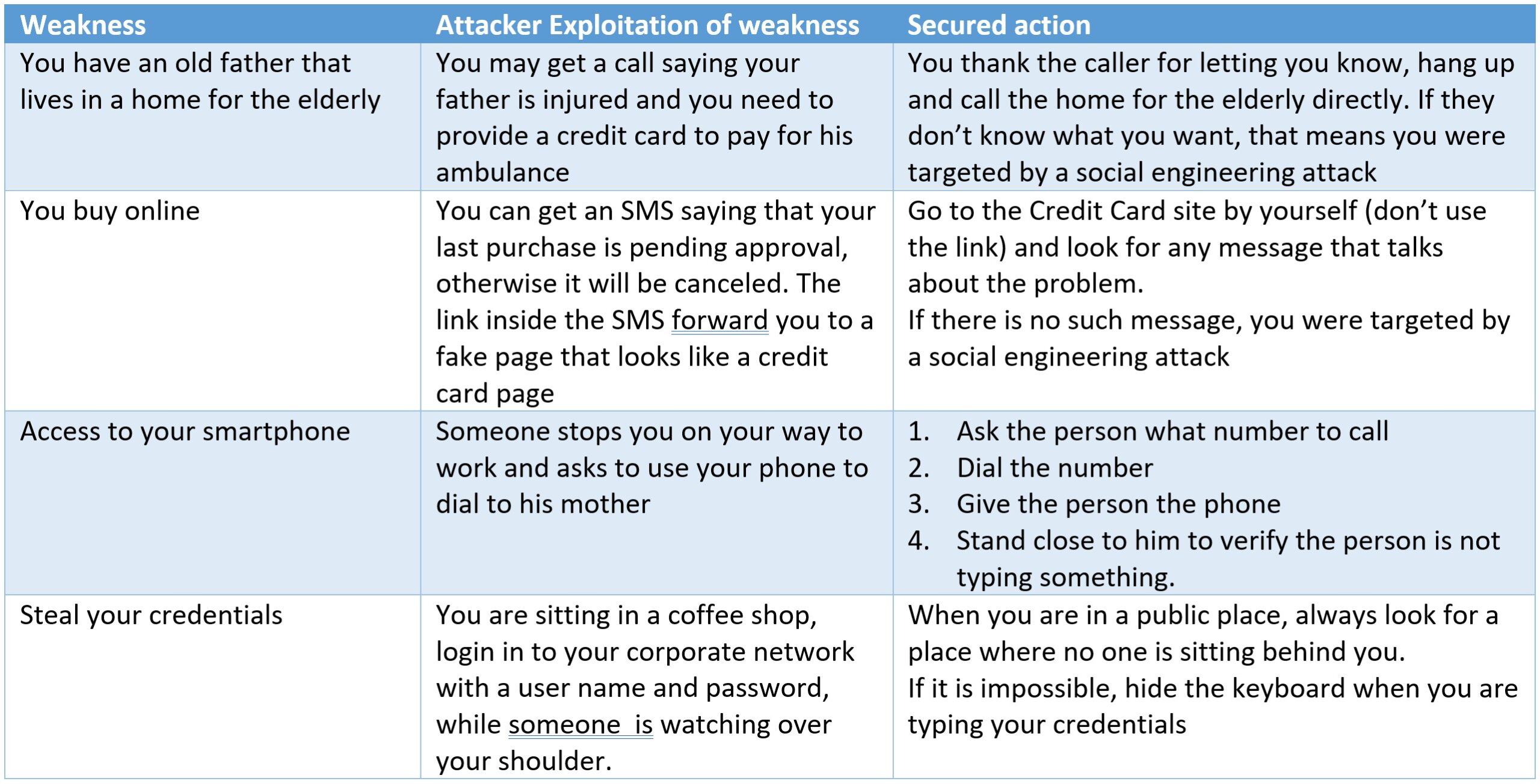
As you can see, it can be easy to protect yourself. I recommend following below guidelines:
1. Trust only who you know2. Never click on any link, if needed, go to the original site by yourself,
or make a call by yourself.
3. In most cases, if you just stop for a second and ask yourself, is it real,
your common sense will do the rest
Stay safe,
Tomer
Thanks for your blog, nice to read. Do not stop.
I have to thank you for the efforts you have put in writing this site. I really hope to view the same high-grade content by you later on as well. In fact, your creative writing abilities has inspired me to get my very own blog now 😉
An intriguing discussion is worth comment. I do think that you should publish more on this topic, it might not be a taboo subject but generally people dont speak about such subjects. To the next! Cheers!!